Encryption essentials: How Xurrent puts you in control of your data

SOC 2
ISO 27001 and ISO 27018
ITIL
GDPR
HIPAA
BYOK
FedRAMP
C5
That’s a lot of letters, a lot of acronyms.
Yet every single one of them (and more) is highly relevant for those in the Service Management space … and especially those who are concerned with compliance, privacy, and security.
In our most recent edition of SMU (Service Management Unlocked), Jim Hirschauer, Xurrent’s Head of Product Marketing, and Tuan Vu, Xurrent’s Training & Enablement Specialist, Global, explore how this alphabet soup of terms impacts today’s global enterprise.
Skip the recap and watch the full webinar? Sure. Here is the link.
What is encryption, and why should you care?
Encryption is the process of converting data into a secure format that can only be accessed with a decryption key.
Think of encryption as a locked box, a box in which only the “right key” can open it.
Most SaaS platforms have Platform Managed Keys, encryption keys that are securely created, stored, and managed by the service provider to protect your data automatically.
Platform Managed Keys are the baseline level of security that does not require user configuration. Think: WhatsApp, Slack, Zoom, and most cloud storage platforms.
With Platform Managed Keys, there is no need for key management, the setup is quick and easily scalable, and you are ensured consistent, provider-managed encryption.
Great. So moving on, right?
Not so fast.
There is another — significantly better — option.
Welcome to BYOK (Bring Your Own Key)
BYOK is a cloud security model that allows customers to use their own encryption keys rather than relying solely on the encryption provided by the cloud service provider.
Said another way, BYOK allows you to control your own encryption keys to secure your own data in the cloud.
And right now, only a handful of ITSMs offer BYOK.
BYOK is most often used in highly regulated industries such as finance and healthcare, where strict compliance (HIPPA, DORA, etc) is paramount.
Why BYOK? Simply put, it offers:
- Complete control over encryption and decryption
- The ability to revoke access to data at any time
- Enhanced compliance with stringent security policies
As mentioned, Xurrent offers BYOK. Here is a snapshot of how it works:
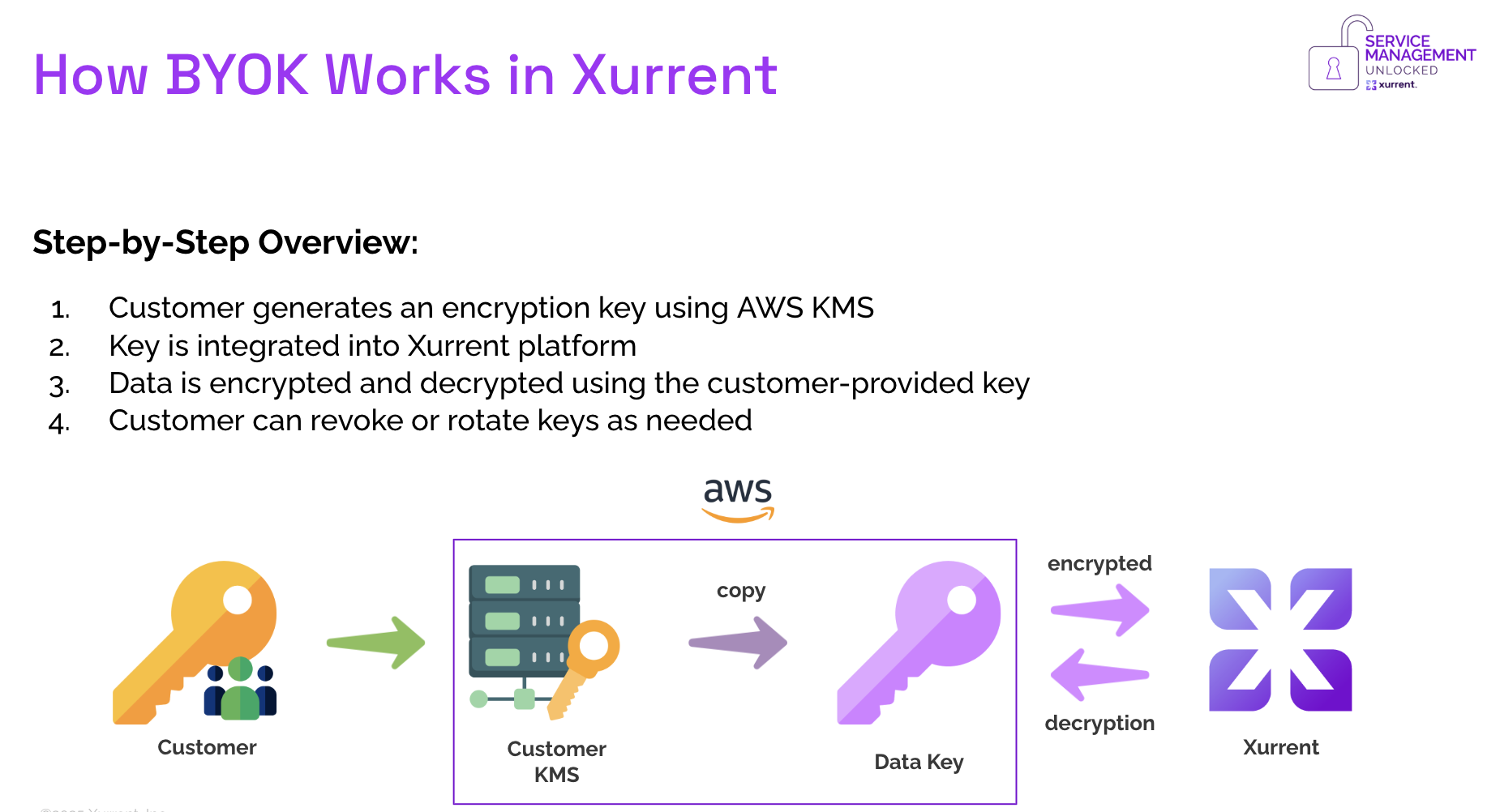
BYOK is only the tip of the security iceberg.
The remainder of the webinar unearthed other ways Service Management providers ensure data is safe and secure (and in compliance with all applicable laws and regulations).
Jim and Tuan discussed C5 attestation, AWS KMS (more acronyms!), the connection between compliance and audit trails, and more.
At the end of the day, Xurrent believes your data is, well, your data.
Watch the full webinar now or chat with one of our experts to learn more.

Moving from Slack OAuth 1.0 to OAuth 2.0: What’s Changing and Why It Matters
As part of our continued commitment to security, transparency, and better integration experiences, Xurrent IMR is updating its Slack integration from OAuth 1.0 to OAuth 2.0. This update ensures our users benefit from the latest in security sta


Xurrent named a Market Leader in Research In Action’s Vendor Selection Matrix™ for IT & Enterprise Service Management Solutions
Xurrent earns #1 rankings in customer satisfaction, price vs value, and recommendation index in Research In Action's global ITSM/ESM Vendor Selection Matrix report.


